Advanced Cyber Threat Analytics: Proactive Defense in a Digital World
In today’s interconnected digital landscape, organizations face an ever-evolving barrage of cyber threats. Reactive security measures, while necessary, are no longer sufficient to protect against sophisticated attacks. This is where advanced cyber threat analytics comes into play. It’s not just about detecting threats; it’s about understanding them, predicting them, and proactively mitigating their impact. This article explores the principles, methodologies, and benefits of leveraging advanced cyber threat analytics to bolster your organization’s security posture.
Understanding Cyber Threat Analytics
Cyber threat analytics encompasses the processes and technologies used to identify, analyze, and understand potential threats to an organization’s IT infrastructure and data. It moves beyond simple signature-based detection to incorporate behavioral analysis, machine learning, and threat intelligence to uncover hidden patterns and anomalies that indicate malicious activity. The goal is to transform raw data into actionable insights, enabling security teams to respond effectively and prevent future incidents.
The Evolution from Reactive to Proactive Security
Traditional security models are primarily reactive, relying on firewalls, antivirus software, and intrusion detection systems to block known threats. However, these tools are often ineffective against zero-day exploits and advanced persistent threats (APTs) that are designed to evade detection. Advanced cyber threat analytics shifts the focus to proactive security, enabling organizations to anticipate and prevent attacks before they cause significant damage. This is achieved by continuously monitoring network traffic, user behavior, and system logs for suspicious activity, and then correlating this data with threat intelligence feeds to identify potential risks.
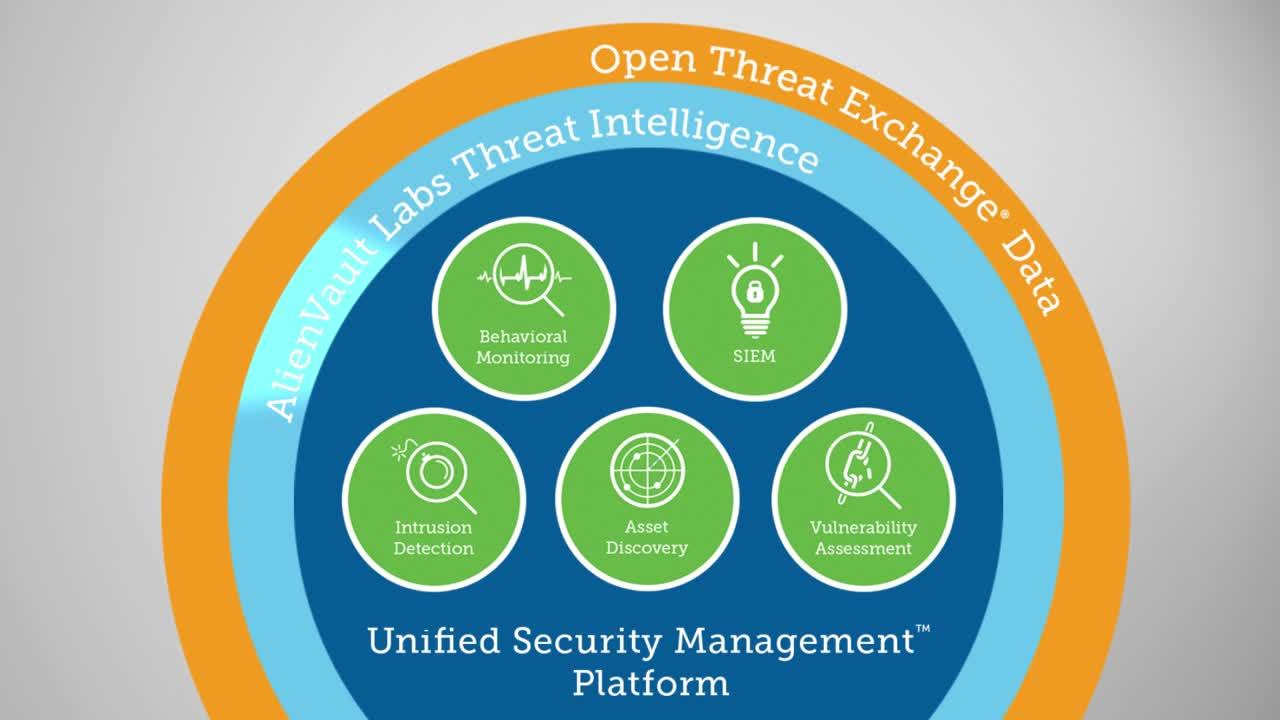
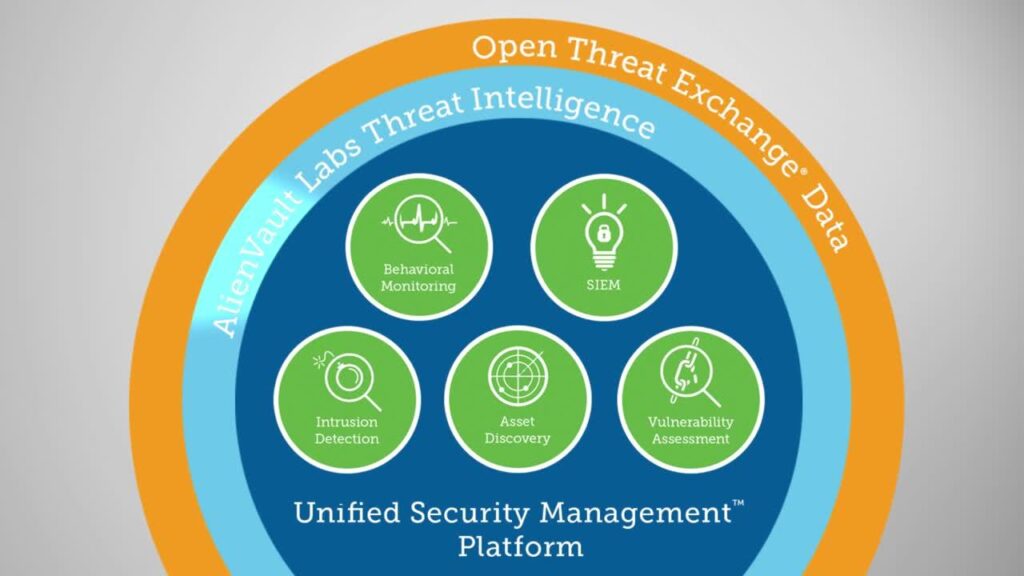
Key Components of Advanced Cyber Threat Analytics
A robust advanced cyber threat analytics program typically consists of several key components, each playing a crucial role in the overall threat detection and response process:
- Data Collection: Gathering data from various sources, including network traffic, system logs, endpoint activity, and cloud services. This data provides the raw material for analysis.
- Data Processing and Storage: Processing and storing the collected data in a scalable and efficient manner. Big data technologies, such as Hadoop and Spark, are often used to handle the large volumes of data generated by modern IT environments.
- Behavioral Analytics: Analyzing user and entity behavior to identify anomalies that may indicate malicious activity. This involves establishing baseline behavior patterns and then detecting deviations from these patterns.
- Threat Intelligence Integration: Incorporating threat intelligence feeds from external sources to stay informed about the latest threats and vulnerabilities. This information is used to enrich the analysis and improve the accuracy of threat detection.
- Machine Learning: Applying machine learning algorithms to automate the detection of complex threats and improve the accuracy of threat predictions. Machine learning can identify patterns and anomalies that would be difficult or impossible for humans to detect manually.
- Visualization and Reporting: Presenting the results of the analysis in a clear and concise manner, enabling security teams to quickly understand the threats and take appropriate action. Visualization tools can help to identify trends and patterns that might otherwise be missed.
Benefits of Implementing Advanced Cyber Threat Analytics
Implementing advanced cyber threat analytics offers numerous benefits to organizations, including:
- Improved Threat Detection: By analyzing large volumes of data and applying advanced analytics techniques, organizations can detect threats that would otherwise go unnoticed.
- Faster Incident Response: Advanced cyber threat analytics provides security teams with the information they need to respond quickly and effectively to security incidents. This can help to minimize the impact of attacks and reduce the cost of recovery.
- Proactive Security: By predicting and preventing attacks before they occur, organizations can significantly reduce their risk of becoming a victim of cybercrime.
- Enhanced Security Posture: Advanced cyber threat analytics helps organizations to identify and address vulnerabilities in their IT infrastructure, thereby improving their overall security posture.
- Compliance: Many regulatory frameworks require organizations to implement security measures to protect sensitive data. Advanced cyber threat analytics can help organizations to meet these requirements.
- Reduced Costs: By preventing attacks and minimizing the impact of security incidents, organizations can reduce the costs associated with cybercrime.
Implementing Advanced Cyber Threat Analytics: A Step-by-Step Guide
Implementing advanced cyber threat analytics can be a complex undertaking, but it doesn’t have to be overwhelming. Here’s a step-by-step guide to help you get started:
- Define Your Objectives: What are you trying to achieve with advanced cyber threat analytics? Are you trying to improve threat detection, speed up incident response, or enhance your overall security posture? Clearly defining your objectives will help you to focus your efforts and measure your success.
- Assess Your Current Security Posture: What security measures do you currently have in place? What are your strengths and weaknesses? Identifying your current security posture will help you to determine where you need to focus your attention.
- Identify Your Data Sources: What data sources do you need to collect to support your advanced cyber threat analytics program? This may include network traffic, system logs, endpoint activity, and cloud services.
- Choose Your Technology: There are many different cyber threat analytics tools and platforms available. Choose the technology that best meets your needs and budget. Consider factors such as scalability, performance, ease of use, and integration with your existing security infrastructure.
- Develop Your Use Cases: What specific threats do you want to detect and prevent? Develop use cases that describe the scenarios you want to address with advanced cyber threat analytics.
- Configure Your System: Configure your cyber threat analytics system to collect, process, and analyze the data you need to support your use cases.
- Train Your Staff: Train your security team on how to use the cyber threat analytics system and how to respond to security incidents.
- Monitor and Refine: Continuously monitor your cyber threat analytics system and refine your use cases based on your findings.
Challenges and Considerations
While advanced cyber threat analytics offers significant benefits, there are also some challenges and considerations to keep in mind:
- Data Volume and Complexity: Analyzing large volumes of data can be challenging, requiring significant computing resources and expertise.
- False Positives: Cyber threat analytics systems can generate false positives, which can waste time and resources. It’s important to tune your system to minimize false positives.
- Evolving Threats: Cyber threats are constantly evolving, so it’s important to stay up-to-date on the latest threats and vulnerabilities.
- Skills Gap: Implementing and managing advanced cyber threat analytics requires specialized skills and expertise.
- Privacy Concerns: Collecting and analyzing data can raise privacy concerns. It’s important to ensure that you are complying with all applicable privacy regulations.
The Future of Cyber Threat Analytics
The field of cyber threat analytics is constantly evolving, driven by the increasing sophistication of cyber threats and the rapid pace of technological innovation. Some of the key trends shaping the future of cyber threat analytics include:
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are playing an increasingly important role in cyber threat analytics, enabling organizations to automate the detection of complex threats and improve the accuracy of threat predictions.
- Cloud-Based Analytics: Cloud-based analytics platforms are becoming increasingly popular, offering scalability, flexibility, and cost-effectiveness.
- Threat Intelligence Sharing: Organizations are increasingly sharing threat intelligence with each other to improve their collective security posture.
- Automation and Orchestration: Automation and orchestration tools are being used to automate incident response and streamline security operations.
- XDR (Extended Detection and Response): XDR platforms are integrating security data from multiple sources to provide a more comprehensive view of the threat landscape. [See also: Understanding XDR: The Future of Threat Detection]
Conclusion
Advanced cyber threat analytics is an essential component of a modern security strategy. By leveraging data, analytics, and threat intelligence, organizations can proactively defend themselves against sophisticated cyber attacks. While implementing advanced cyber threat analytics can be challenging, the benefits are significant. By following the steps outlined in this article, organizations can successfully implement advanced cyber threat analytics and improve their overall security posture. Organizations must embrace these advanced techniques to stay ahead of the ever-evolving threat landscape. Investing in advanced cyber threat analytics is not just a security measure; it’s a strategic imperative for survival in the digital age. The proactive nature of advanced cyber threat analytics allows businesses to anticipate and neutralize threats before they escalate, minimizing potential damage and ensuring business continuity. As cyber threats become increasingly complex, the need for sophisticated analytical tools and strategies will only continue to grow, making advanced cyber threat analytics a cornerstone of effective cybersecurity.